Research Areas
Current Research
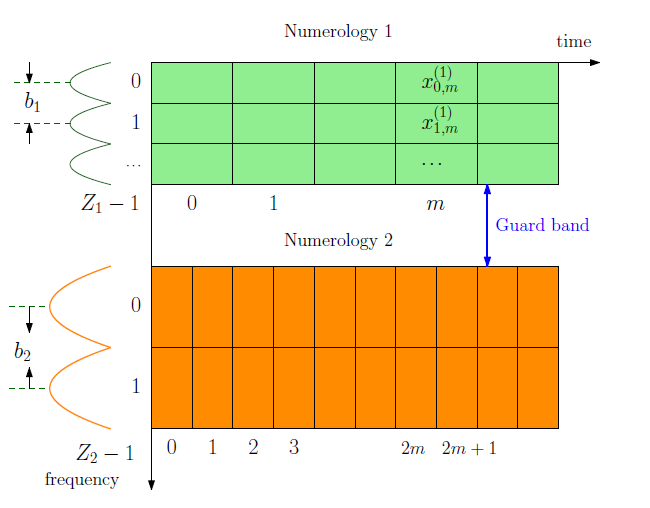
Mixed numerology has been adopted in the orthogonal frequency division multiplexing (OFDM)-based physical layer of 5G new radio (NR) to serve diverse use cases and services. The numerology of the OFDM waveform refers to the specific parameters of the subcarrier spacing, OFDM symbol duration, and CP duration. 5G NR uses a flexible OFDM waveform with subcarrier spacings ranging from 15 kHz up to 960 kHz, with a proportional reduction in OFDM symbol and CP durations. In mixed-numerology OFDM, the entire system bandwidth is divided into non-overlapping bandwidth parts. Each bandwidth part can be assigned a distinct numerology. The numerology chosen for a user depends upon the type of service and the frequency band of operation. The resource grid of a mixed-numerology system with two numerologies is shown in Fig. 1. When mixed-numerology OFDM systems operate over the channels envisioned for 5G, they face two kinds of interference, due to the use of the OFDM waveform. These are inter-numerology interference (INI) and inter-carrier interference (ICI).
We focus on analysing INI and ICI in wideband time-varying channels in the presence of phase noise. For SISO systems, we derive expressions for the fading-averaged INI and ICI powers at each subcarrier. To mitigate INI and ICI, we develop subcarrier power allocation method that exploits the variation in the INI and ICI powers across the subcarriers. For MIMO systems, we derive expressions for the INI and ICI covariances in a wideband spatially correlated time-varying channel with phase noise. With this analytical foundation, we develop a joint INI and ICI mitigation technique that is based on statistical information and incorporates fairness. We derive the precoder for each user that achieves the single-user ergodic capacity and determine an eigenmodes power allocation for the users that maximizes the weighted sum rate.
Members: Venkata Satya Sreedhar T.
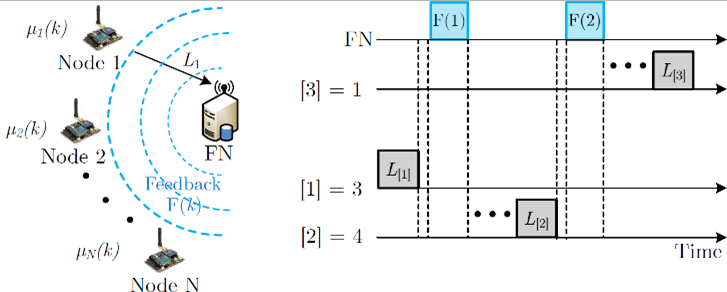
Distributed fusion in wireless sensor networks has applications in diverse fields such as surveillance, healthcare, environmental monitoring, inventory management, transportation, and logistics. In these networks, spatially distributed sensor nodes make measurements and communicate some or all of them to a fusion node, which makes further computations. While the fusion node is often connected to the power grid, the sensor nodes are powered by batteries whose energies drain out over time. Therefore, improving energy-efficiency, which leads to a longer network lifetime, is a critical issue in these applications. Protocols such as censoring, on-off keying, duty cycling, and clustering improve the energy-efficiency by curtailing the number of nodes that transmit. However, this invariably leads to a degradation in performance. We propose energy-efficient data fusion protocols for wireless sensor networks. Our aim is to develop novel, insightful analytical characterizations of these protocols to evaluate key performance measures such as probability of error and average number of transmissions.
We exploit the idea that distributed fusion with fewer but informative measurements can achieve the same level of accuracy compared to the conventional case when all the nodes transmit their measurements to the fusion node. The novelty of our work lies in the design of a metric that decides how informative a measurement is and the subsequent data fusion algorithm at the fusion node. A combination of these two contributions not only achieves energy-efficiency, but also ensures that the network performance is not compromised. For the binary hypothesis testing problem, we propose a novel feedback-enhanced successively reordered transmissions scheme (FE-SRTS). In this scheme, the node with the highest absolute value of log-likelihood ratio (LLR) first transmits its LLR to the fusion node. The fusion node either decides early or broadcasts the LLR it received to all the nodes. The feedback is used to reorder the sequence of nodes that transmit. The node whose LLR is the farthest from the fed back LLR transmits next. The fusion node either decides or feeds back, as above, its last received LLR. This process continues until the fusion node decides. The ordering is implemented in a decentralized manner using the timer scheme, which ensures that no node, including the fusion node, has to know the LLR of other node.
|
Members: Sayantan Adhikary
Federated learning is a distributed technique that allows multiple devices to collaboratively train a shared or global machine learning model. In this iterative technique, each device computes a local model (or gradient) based on the current global model and its local dataset that comprises of data and their corresponding labels, and shares this local model with a cloud-based parameter server.
Over-the-air computation-assisted federated learning (OTA-FL) is an aggregation technique that exploits the superposition principle of the wireless multiple-access channel to compute the global model from multiple uplink transmissions. However, a key difference compared to conventional learning scheme is that the learning algorithm's performance depends on the channel gains between the devices and the parameter server, the transmit power of the devices, the receiver scaling, and noise at the parameter server.
Typically the learning performance is characterized by the optimality gap which is the difference between the minimum value of the loss function, if the data were centrally available at the parameter server, and the loss function given the current model computed over the data sets of all devices. We develop a novel energy-efficient joint device transmit power adaptation and receiver scaling scheme that ensures a guaranteed rate of convergence of the optimality gap while minimizing the accumulated resdual error that arises due to batch selection and wireless noise.
Members: Sayantan Adhikary
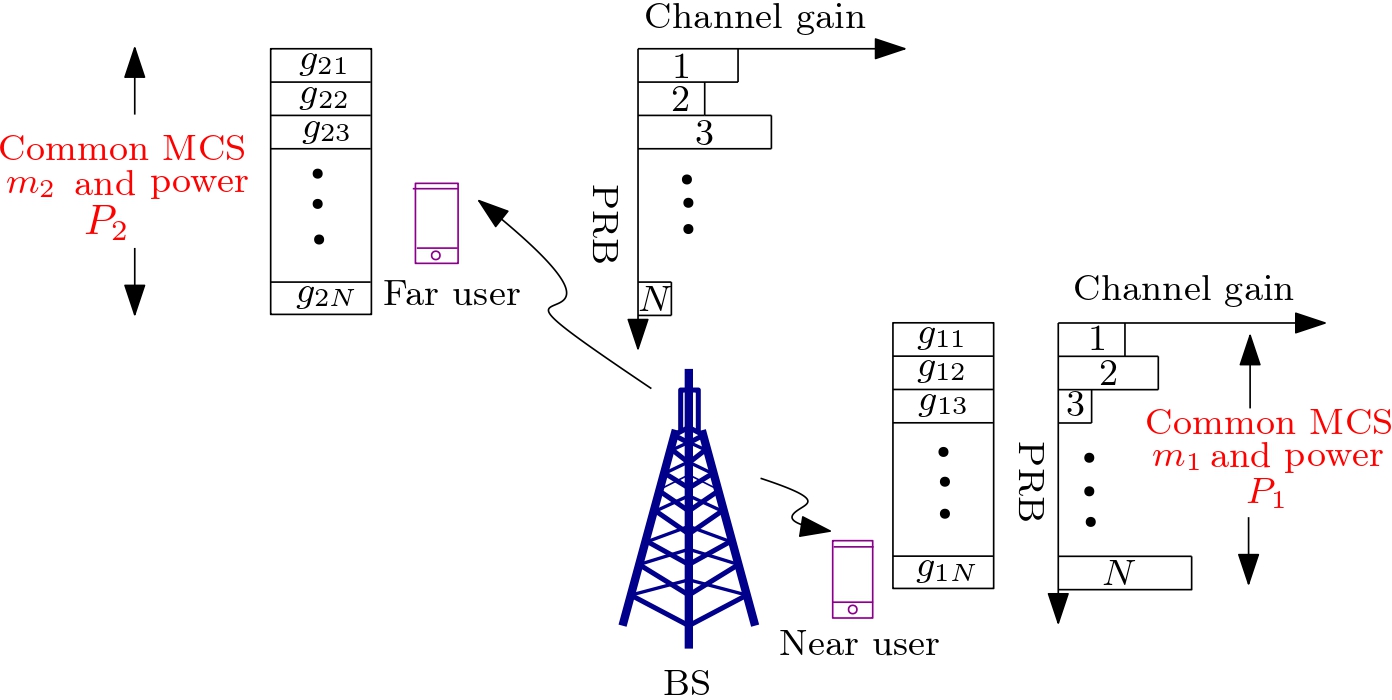
Emerging technologies such as full-duplex radio, sidelink communications, massive multi-antenna systems, network-controlled relaying, and non-orthogonal multiple access (NOMA) are central to the evolution of 5G New Radio (NR) and future wireless networks. Among these, power-domain NOMA offers a promising approach to enhance spectral efficiency and user fairness. In power-domain NOMA, a base station (BS) serves multiple users simultaneously over the same time-frequency resources by superimposing their signals at different power levels. Users with better channel conditions apply successive interference cancellation (SIC) to decode and remove interfering signals before decoding their own, while others treat interference as noise. For example, in a two-user NOMA scenario, the near user decodes and cancels the far user's signal before retrieving its own, whereas the far user decodes its data with interference from the near user.
NOMA offers several advantages over traditional orthogonal multiple access (OMA), including improved spectral efficiency, reduced transmission delays, enhanced cell-edge throughput, and better user fairness. For deployment within the 5G NR framework, NOMA must be integrated with orthogonal frequency division multiplexing (OFDM). In OFDM-based systems, the available bandwidth is partitioned into physical resource blocks (PRBs), which are allocated to users according to their data requirements. However, 5G standards impose a constraint whereby each user must employ a common modulation and coding scheme (MCS) and transmission power across all assigned PRBs. This constraint simplifies system design by reducing feedback and control signaling, but also introduces new challenges in performance optimization.
Our research focuses on determining the optimal power allocation and discrete rate selection for near and far users in power-domain NOMA in frequency-selective channels, under block error rate (BLER) constraints. We analyze the average weighted sum rate of the above system, providing insights into practical NOMA deployment strategies in future wireless networks.
|
Members: Sruthy S.
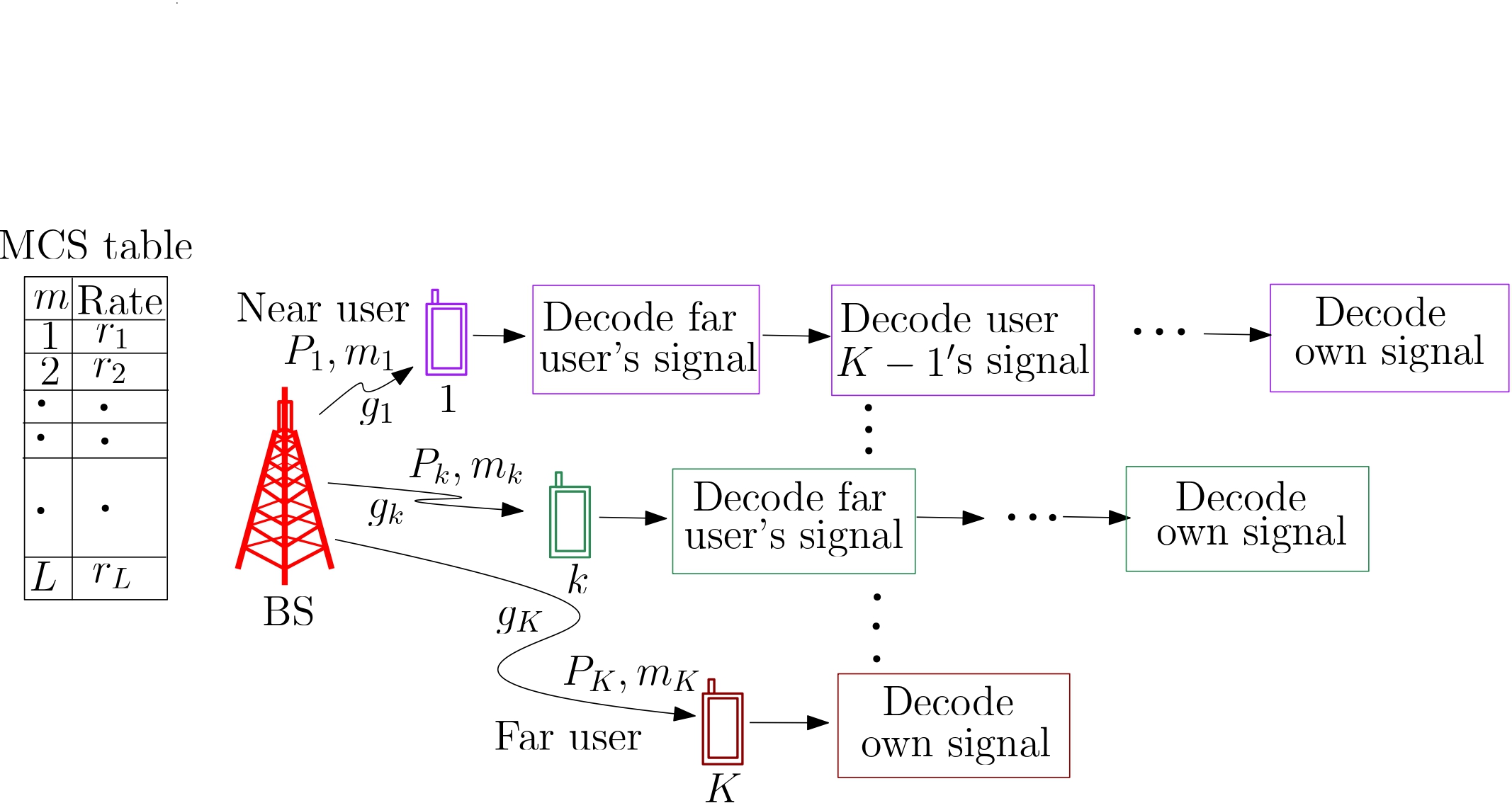
The performance of downlink non-orthogonal multiple access (NOMA) is significantly impacted by practical physical layer limitations such as discrete rate adaptation and imperfect successive interference cancellation (SIC). Our research investigates how these factors influence the spectral efficiency and fairness of NOMA systems, which differ fundamentally from conventional orthogonal multiple access (OMA) schemes used in current 5G networks. The effectiveness of NOMA is determined by several key aspects:
1. Utility Function Design: The system-wide utility function governs how power and rate are allocated to users. Common utility functions include sum rate, weighted sum rate, proportional fairness, and max-min fairness.
2. Discrete Rate Adaptation: Unlike the idealized continuous-rate models based on Shannon capacity, practical systems must choose modulation and coding schemes (MCSs) from a finite set.
3. Imperfect SIC: In theory, SIC should perfectly cancel interference from previously decoded signals. However, real-world conditions such as channel fading, noise, and hardware limitations-can lead to decoding errors.
4. Decoding Order: The order in which users' signals are decoded plays a critical role.
Our work focuses on jointly optimizing power allocation, rate selection, and decoding order in a K-user downlink NOMA system. We aim to maximize a generalized weighted \( \alpha \)-utility function while satisfying block error rate (BLER) and minimum rate requirements for each user. For the widely studied two-user case with a farthest-to-nearest decoding order, we derive novel expressions for outage probability, average sum rate, and \( \alpha \)-utility, providing deeper insights into NOMA system design under realistic conditions.
|
Members: Sruthy S.

|
|
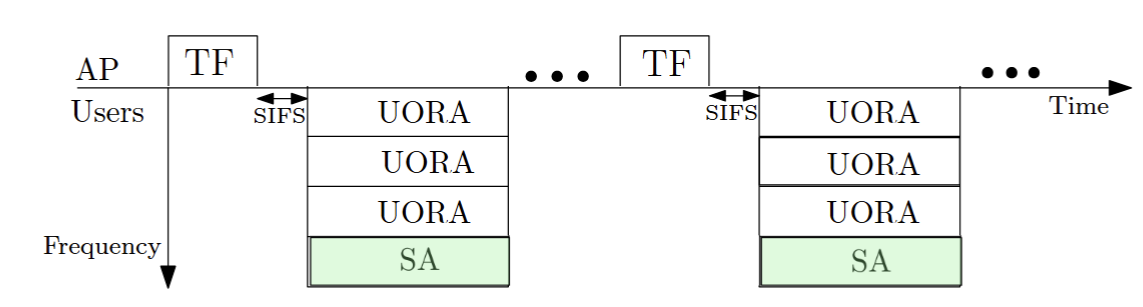
Wireless fidelity (Wi-Fi) has evolved to facilitate connectivity for billions of devices and is the preferred choice for internet access among users. The most recent amendment of Wi-Fi is IEEE 802.11be. It incorporates several innovative physical (PHY) and medium access control (MAC) layer techniques that were introduced in the IEEE 802.11ax, which prioritized enhanced capacity and reduced latency in dense deployments. These include orthogonal frequency division multiple access (OFDMA) in the PHY layer. These also include hybrid access in the MAC layer, which consists of concurrent, contention-free uplink transmissions through scheduled access (SA) and contention-based uplink OFDMA random access (UORA).
A key aspect of hybrid access is trigger frames (TFs), through which the access point (AP) broadcasts RU allocation for SA and UORA and user scheduling information. Hybrid access with three RUs for UORA and one RU for SA is shown in Fig. 1. In SA, the AP schedules the users on the SA RUs based on the buffer status reports (BSRs) sent by the users in UORA. SA improves the overall throughput while UORA enables users to enter SA. Another key innovation in 802.11be is multi-link (ML) operation. It allows an ML device to transmit and receive data on more than one selected link as depicted in Fig. 2. The benefits of ML include improved spectral efficiency, higher data throughput, and lower latency.
Our goal is to understand the optimal use of the above key features combined. Our approach will lead to a novel and insightful analysis of the saturation throughput, head-of-line delays, and latency of the upcoming 802.11be protocol.
Members: Arthi S.
Fifth-generation(5G) wireless systems are designed to provide diverse services such as enhanced mobile broadband (eMBB), massive machine-type communication, and ultra-reliable and low latency communications (URLLC). Among these, URLLC mandates error rates as low as 0.001% and latencies as small as 1 ms. It enables new applications such as industrial automation, autonomous vehicles, telesurgery, and tactile internet.
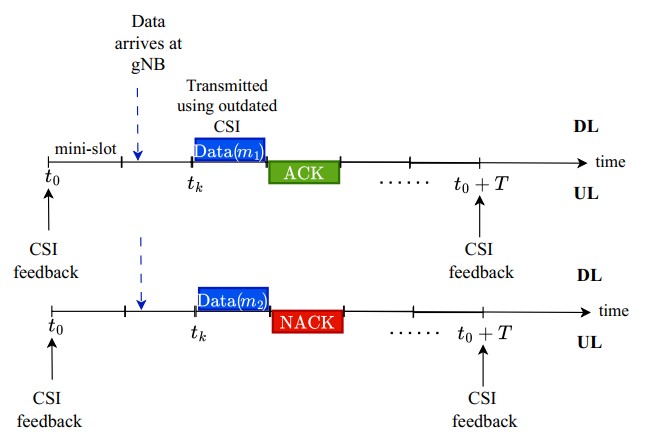
The latency-critical URLLC data is transmitted immediately upon arrival at the base station. It chooses the modulation and coding scheme (MCS) as a function of channel state information (CSI) periodically fed back by the user. The CSI feedback gets partially outdated due to the time-varying nature of the channel. URLLC data is transmitted by puncturing the resources of ongoing eMBB transmissions. This leads to an increase in the BLER and a reduction in the eMBB data rate. We develop a novel approach to assign time-frequency resources to the URLLC user to meet tight constraints while minimizing the resources taken away from the existing eMBB traffic.
Given the extremely low error probabilities envisaged for URLLC, a Monte Carlo-based simulation becomes impractical due to the extremely large number of samples it requires. We develop other sampling techniques with low sample complexity to simulate the low BLERs.
|
Members: Sandeep Issarapu
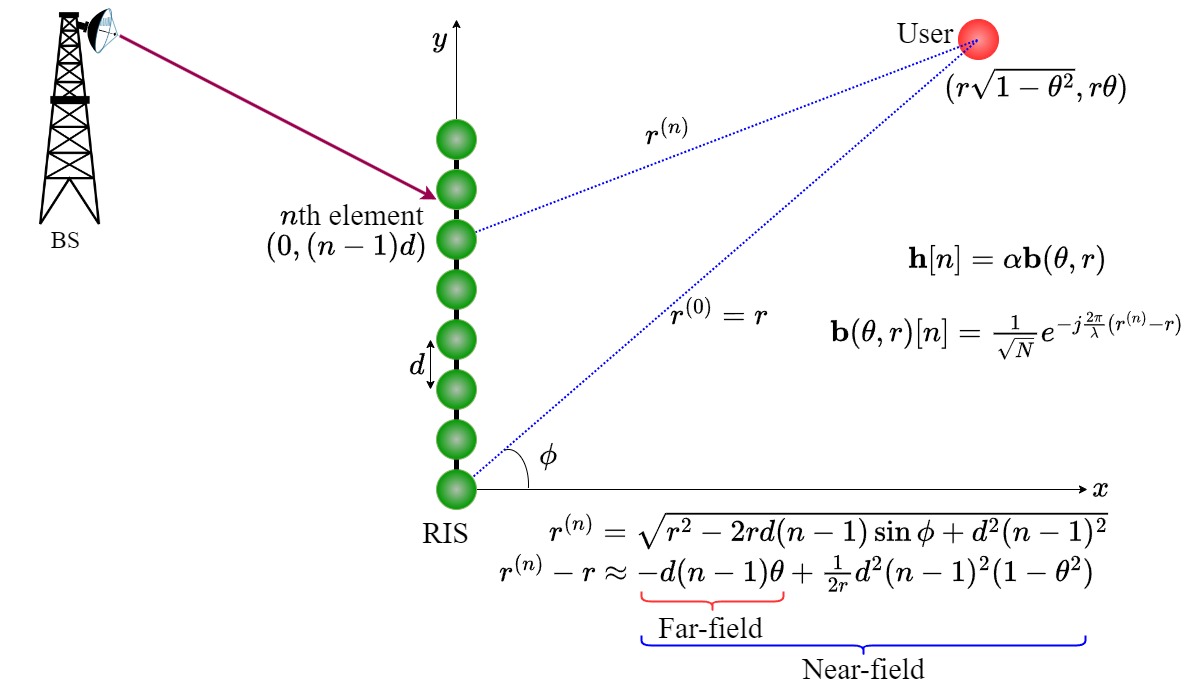
Upcoming wireless generations are expected to deploy extremely large aperture antenna arrays (ELAAs) at the base station (BS). They are also expected to operate at high carrier frequency ranges, including the FR2 and FR3 bands. The combined effect of higher carrier frequency and ELAA leads to the users lying in the near-field of the ELAA. This is because the Fraunhofer distance which separates the near-field, and the far-field increases as the product of the square of aperture and the frequency. Unlike the conventional far-field communication systems, where the signal wavefronts are parallel, the signal wavefronts are spherical in the near-field region. As a result, the steering vector of the near-field channel now depends not only on the angle-of-arrival/departure, but also on the distance between the ELAA and the user. This is contrary to the conventional far-field channels, where the steering vector depends only on the angle-of-arrival/departure.
The rudimentary change in the channel definition makes it necessary to revisit the channel estimation protocols that are specific to the near-field channels. These channel estimates are necessary for the precoding, combining, and coherent data demodulation. In this work, we study the near-field channel estimation protocols for the scenario where the user lies in the near-field of a reconfigurable intelligent surface (RIS). Here, the channel gains are required not only for the coherent data demodulation, but also for configuring the RIS phase configurations. We study the cumulative effect of the noisy channel estimates used to set the RIS configuration and that of the BS-RIS-user effective channel gain on the performance metrics such as achievable rate. We also study the trade-offs between the data-pilot powers and duration resource allocation.
|
Members: Shivani Dhok
Previous Research
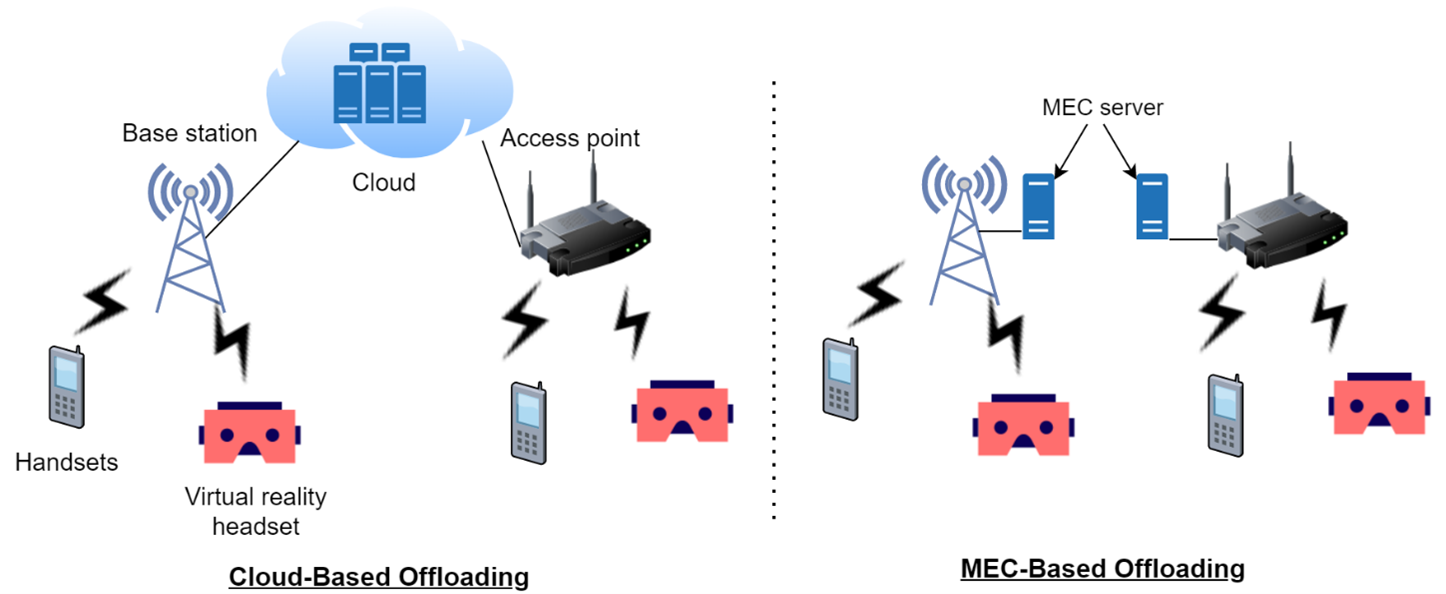
Mobile edge computing (MEC) is one of the emerging paradigms for next generation communication systems. MEC provides a solution to meet the ever-increasing demands of low latency and increased computation power by advanced applications such as augmented reality (AR), virtual reality (VR), and vehicle-to-cloud (V2C) networks. Each application has its own requirements. For example, AR and VR applications require a latency of less than 20ms, and V2C enabled networks demand latencies as low as 10ms. MEC caters to such strict demands by bringing the server to the edge of the network, thereby decreasing network latency.
Handsets that cannot handle low-latency, computationally-intensive applications due to their limited computation capabilities and energy constraints can now offload their tasks to MEC servers as depicted in Figure 1. With handsets capable of supporting multiple radio access technologies (RATs), such as wireless local area network (WLAN), 4th generation long-term evolution (LTE), and 5th generation new-radio (5G-NR), they can access multiple MEC servers through these multiple RATs. Each RAT has a different access technology and its own capabilities. For example, LTE and 5G-NR provide dedicated channel resources by reserving orthogonal subchannels for every user admitted into its network. On the other hand, WLAN adopts a random-access method based on the IEEE 802.11 media access control (MAC) protocol, in which users contend with each other to access the channel. While a cellular network can accommodate up to a certain number of users, the WLAN places no such hard restriction. However, the WLAN access delays increase as the number of contending users increases.
In the MEC literature, a common assumption which is prevalent is ignoring the WLAN contention delays or modelling the WLAN like a cellular network by limiting the number of users that can access it. We aim to work on this research gap by accurately modelling the 802.11 MAC protocol. Thereafter, we focus on developing policies that determine when a user should offload its task as well as which RAT should it choose to process as many tasks as possible with minimal latency.
Members: Rushabha B.
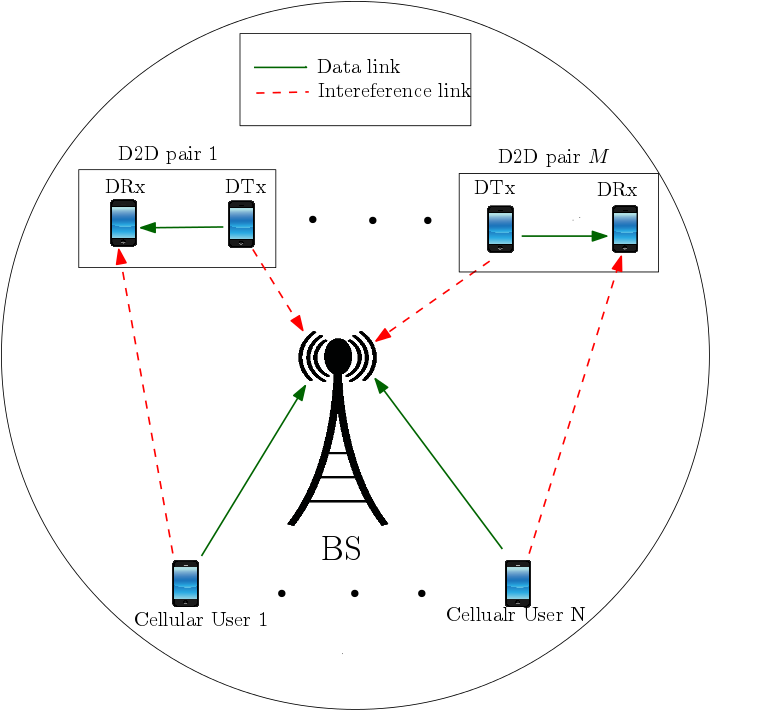
Device-to-device (D2D) communication is a promising solution for next generation cellular systems, in which D2D users share the available spectrum with the cellular users under the control of the base station. The D2D users can bypass the base station and can communicate with each other directly. D2D communication is practically appealing because it reduces the traffic load on the base station, improves frequency reuse, increases cell throughput, and reduces latency.
Given a set of user equipments, some of which are D2D pairs and the rest are CUs, several new challenges such as mode selection, user scheduling, rate adaptation, subchannel allocation, and power control arise. Mode selection involves determining whether an subchannel should be allocated to only a D2D pair (Dedicated Mode); to only a cellular user (Cellular Mode); or to both together (Underlay Mode). A critical problem that arises due to the addition of D2D users in the cell is that, in underlay mode, additional co-channel interference due to simultaneous data transmissions from the cellular user and the D2D pairs reduces the cell throughput.
A critical and common assumption is that the complete instantaneous channel state information of all the links is available at the base station including the channel state information of the interference link between cellular user and D2D receiver. This assumption increases the feedback overhead in the system. Hence, our focus is to analyze the methods that reduce the interference link feedback overhead in the system, optimal resource allocation by the base station when it has partial channel state information, and an evaluation of their ability to improve cell throughput.
Members: Sai Kiran B., Bala Venkata Ramulu G.
Energy-efficiency (EE), which is defined as the number of bits that can be communicated reliably per unit energy consumption, is one of the key performance indicators while designing the next generation wireless communication systems. For example, 5G systems are envisaged to achieve a hundred times higher EE than 4G systems. This is because these systems are required to support applications that demand high data rates, which in turn consumes high energy. Considering the limited battery capacity of the devices, enabling them to communicate larger number of bits per lesser energy consumption is the need of the hour.
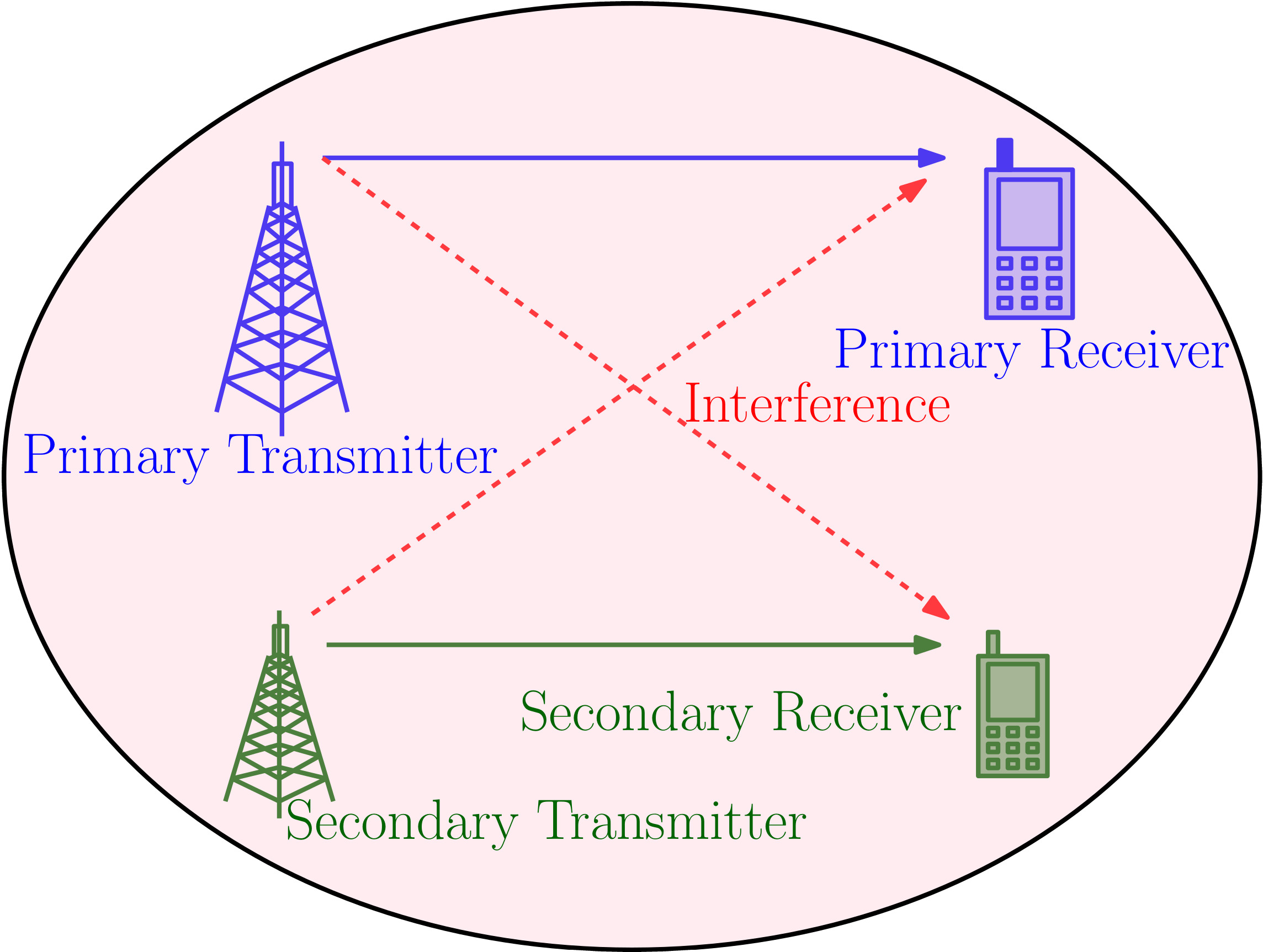
Efficient utilization of spectrum is equally important as efficient utilization of energy while designing a wireless communication system because one of the major challenges that we face today is the scarcity of the available spectrum, especially in the sub-6 GHz band. This makes the underlay spectrum sharing a promising technology in today�s wireless communication systems. In it, a high priority primary user (PU) shares its spectrum with one or more low priority secondary users (SUs) as depicted in Fig. (1). For example, citizens broadband radio service (CBRS) and 5G NR unlicensed utilize spectrum shared by military radar services and satellite services, respectively. However, this brings new design challenges as the constraints on the SU to protect the PU from interference degrade its performance.
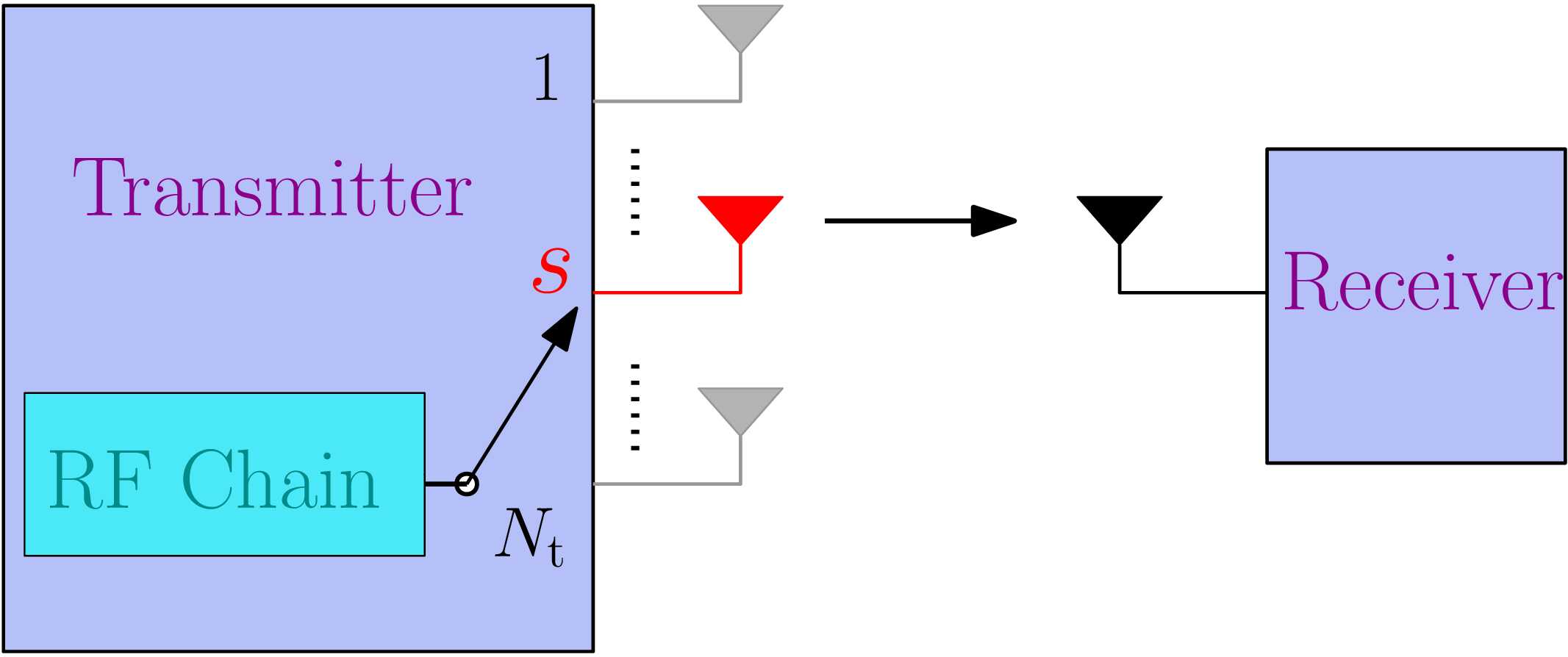
Transmit antenna selection (TAS) can be employed to mitigated the performance degradation caused by the interference constraints at the SU. It is a low-complexity and low -cost, multiple antenna technique that has been adopted in LTE and IEEE 802.11n. In it, one of the transmit antennas is selected based on the channel conditions for transmission as shown in Fig. (2). This reduces the required number of radio frequency (RF) chains. An RF chain consists of components such as filter, mixer, digital-to-analog converter, and power amplifier. Hence, using lesser number of RF chains reduces the hardware complexity and cost to a great extent.
Considering these factors, we focus on developing an optimal rule that selects antenna and its power at the transmitter side of the SU such that the EE of the SU is maximized. The rule also ensures that the interference at the PU caused by the SU is within the tolerable limit. We also develop efficient algorithms to determine the parameters involved in the rule.
Members: Suji N.
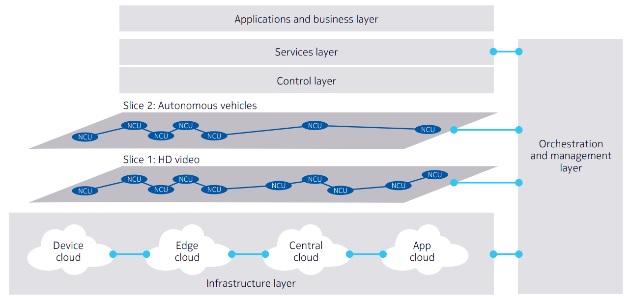
5G has revolutionized traditional mobile communications through its innovative architectural changes, mainly the separation of control and user-plane functions. It uses the service-oriented architecture (SOA) that enables the virtualization of the physical network into multiple logical networks or network slices, in contrast to the traditional �one-size-fits-all� architecture, by leveraging the benefits of software-defined networking (SDN) and network function virtualization (NFV). Thus, network slicing is conceptualized as the creation of multiple virtualized logical networks over a shared physical network. The logical networks spanning across 5G radio access network (RAN), edge, and core can be connected to form an end-to-end network slicing for application-specific service provisioning. Figs. 1 and 2 show illustrative examples of network slicing, where multiple logical networks are created based on application-specific requirements.
|
|
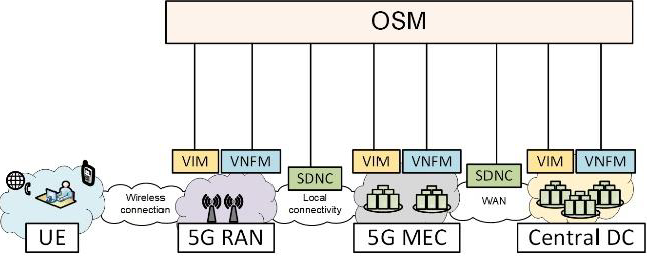
ETSI�s NFV architecture and network management and orchestration (MANO) stack have defined the baseline functionalities and application programming interfaces (APIs) that can be used for network slicing. The MANO framework consists of three primary components � virtual infrastructure manager (VIM), VNF manager (VNFM), and NFV orchestrator (NFVO). The VIM and VNFM manage the virtualized resources and individual virtual network functions (VNFs), respectively. Whereas NFVO manages network services associated with applications by interconnecting the VNFs. The open-source MANO (OSM) is an orchestration and management system that provides a production-quality MANO stack for NFV. Figs. 3 and 4 show an example of next-generation 5G architecture for end-to-end network slicing using OSM and its interaction with VIMs and VNFs, respectively.
|
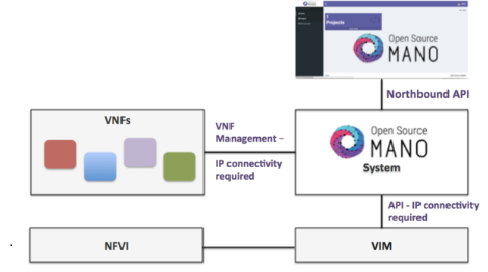
(source:https://osm.etsi.org/docs/user-guide/01-quickstart.html) |
Our ongoing development of an end-to-end network slicing platform for 5G at the lab uses OSM ( https://osm.etsi.org/docs/user-guide/index.html") as network orchestrator, where OpenStack is being used as VIM. To deploy 5G core functionalities, free5Gc (https://www.free5gc.org/) is being used in our implementation. However, we have a plan to include other VIMs as well, such as vim-emulator and Amazon Web services (AWS). The developed platform will be used for prototyping the ongoing research efforts in the lab on end-to-end network slicing in 5G. Fig. 5 shows the GUI of OSM through which network administrators can monitor network services in addition to the standard CLI
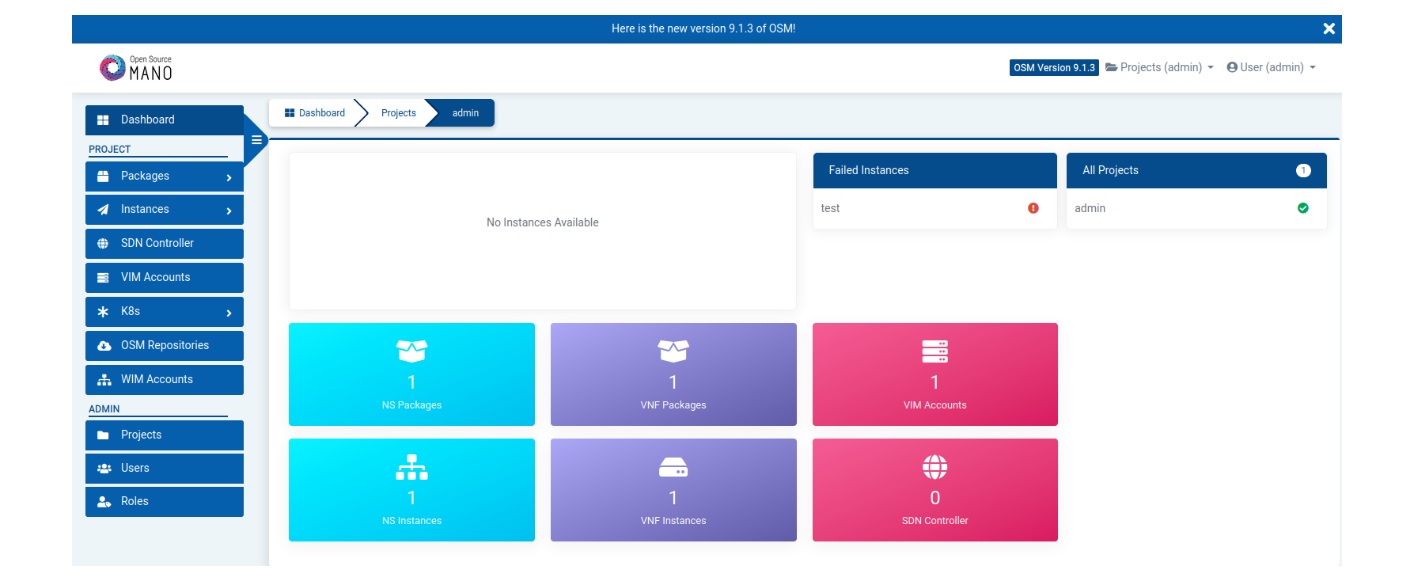
Members: Samaresh Bera
In-band full duplex enhances spectral efficiency and reduces latency of wireless network by enabling simultaneous transmission and reception of the signal at the wireless devices in the network over the same channel.It is a promising technology that enhances the performance of the wireless base stations with small coverage areas. Therefore, it is one of the candidate technologies being considered for 5G cellular networks.
However, several new system design challenges arise in implementing full-dupex in cellular wireless networks. It introduces new interference scenarios in the network. The simultaneous transmission and reception at the wireless device causes transmission power leakage to the receiver of the device, which isknown as self-interference. The self-interference at the receiver degrades signal to noise interference ratio of the received signal and can even drown out the received signal if not cancelled. This self-interference is mitigated by advanced circuit design techniques such as the analog and digital domain signal cancellation, and antenna isolation.Another new source of interference arises because the uplink and downlink users communicate simultaneously over the same channel in networks that employ full-duplex base stations. The simultaneous presence of the uplink with the downlink over the same channel causes cross-link interference to the downlink user.This severity of this interference depends on the scheduling and power control algorithms used at the base station. We are working on the design and performance analysis of cross-link interference-aware radio resource allocation algorithms for scheduling usersand controlling their transmit powers and transmit rates.
Members: Ramakiran
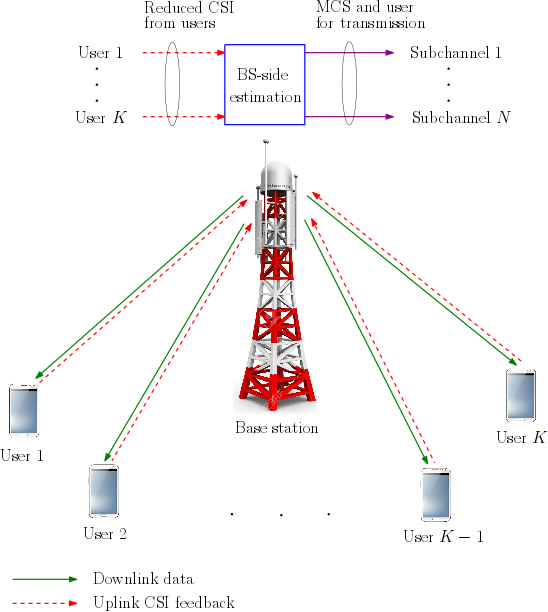
Current and next generation orthogonal frequency division multiplexing-based wireless cellular systems strive to maximize spectral efficiency and meet the increasing demand for higher data rates despite being severely constrained by the limited spectrum availability. Rate adaptation and scheduling are two key enabling techniques employed to achieve these challenging goals. In them, the determination of the user the base station (BS) transmits to and its modulation and coding scheme (MCS) for downlink transmission over a group of subcarriers, which is called a subchannel, is driven by the channel conditions. To do so, the BS requires feedback of channel state information (CSI) from the users in the uplink.
In order to ensure that the feedback overhead does not overwhelm the uplink, several reduced feedback schemes have been proposed in the literature. However, reduced feedback leads to a loss in throughput since CSI available at the BS is not sufficient to effectively carry out rate adaptation and scheduling. We propose novel BS-side estimation techniques to mitigate this loss in throughput. These techniques incorporate statistical information such as mean signal- to-noise ratio and correlation across SCs along with the fed back CSI to systematically determine the MCS and user for transmission.
We consider the practically relevant best-M and threshold-based feedback schemes. In the former, each user feeds back CSI only for its M strongest SCs, while in the latter, each user feeds back the index of the highest rate MCS at which it can reliably receive for each SC. We develop two BS-side estimation techniques, namely, a minimum mean square error estimator- based approach and a throughput-optimal rate adaptation and scheduling policy. The proposed techniques significantly improve the cell throughput without requiring any additional feedback. The throughput-optimal policy also leads to a new benchmark for the achievable cell throughput for the respective feedback schemes. Further, for the threshold- based feedback scheme, it decouples the resolution of feedback from the number of MCSs available at the BS. This enables a system designer to reduce the feedback resolution without lowering the cell throughput by provisioning for more MCSs at the BS.
Members: Jobin Francis, Vineeth Kumar
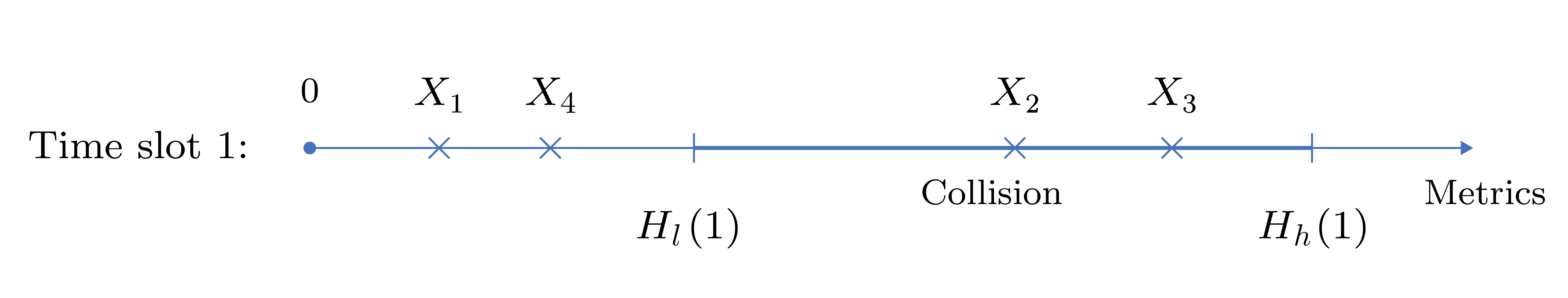
Opportunistic selection which aims to select the best node from a set of available nodes in order to improve the overall system performance has gained attention in many wireless systems such as relay-aided co-operative communication systems, wireless sensor networks, and ad hoc networks. In it, each node possesses a real-valued metric based on which the best node is selected. However, a major challenge that needs to be tackled here is that the nodes are geographically seperated from each other and a node cannot decide by itself if it is the best node. Distributed selection algorithms such as timer-based back-off algorithm and splitting-based selection algorithms have therefore been proposed for this.
The splitting-based selection algorithm is a time-slotted algorithm in which each node locally decides to transmit in a slot if its metric lies between two thresholds. At the end of each slot, a coordinating node called sink feeds back to all the nodes one among the following outcomes: idle (if no node transmitted), success (if exactly one node transmitted), or collision (if two or more nodes transmitted). Based on the feedback, the nodes update their thresholds and the algorithm continues. A success feedback implies that the best node has been selected; hence the algorithm terminates.
The splitting-based selection algorithm has attracted a great deal of research interest due to two reasons (i) it guarantees to select the best node (ii) it is a fast and scalable algorithm as it provably selects the best node in 2.467 slots, on average, even when the number of nodes tends to infinity. However, several other problems related to splitting algorithm remain open and we focus on developing efficient mechanisms to solve these.
Members: Reneeta Sara Isaac
Ordered Transmissions Approach
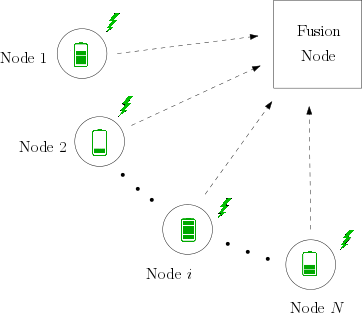
Wireless sensor networks (WSN) are finding increasing applications in environmental monitoring, military surveillance, industrial automation, infrastructure security, smart homes, and intelligent transportation. They consist of sensing nodes that probe the environment and report the sensed data to a fusion node. In the practical deployment of WSNs, running cables to power the sensors is often cumbersome or impractical. Hence, the sensor nodes are equipped with an energy storage device such as a pre-charged battery.
In many applications, the most significant source of energy consumption comes from message transmission. As the sensor nodes transmit data to the fusion node, the energy stored in the batteries gets depleted and eventually the sensor network dies. Therefore, ensuring energy-efficiency is crucial to increase the lifetime of the network. Ordered transmissions is an approach to improve the energy-efficiency. In it, more informative messages are transmitted first followed by lower informative messages. The transmissions are halted upon accumulating sufficient evidence at the fusion node. This reduces the number of transmissions by a factor of at least two without degrading the system's detection performance.
Energy harvesting (EH) is a different approach to address the issue of limited network lifetimes. In the WSNs with EH, the sensor nodes harvest energy from natural or man-made sources in the environment such as solar, thermal, electromagnetic, or mechanical. The harvested energy is used to replenish the batteries of the sensor nodes. Therefore, an EH sensor node no longer permanently runs out of energy in its battery. However, it can occasionally run out of energy, in which case it fails to transmit its messages to the fusion node. These networks, thus, promise perpetual operation and have attracted considerable attention recently.
We focus on the ordered transmissions approach in which some of the transmissions can be missing. This is motivated by the use of EH in WSNs. The absence of the readings requires a new set of decision rules to be used at the fusion node. We develop a new timer scheme to order the transmissions and use the extra information gained from ordering to setup new decision rules. These new rules not only reduce the average number of transmissions but also give better detection performance compared to that of the conventional approach where the transmissions are not ordered.
Members: Sai Kiran P.
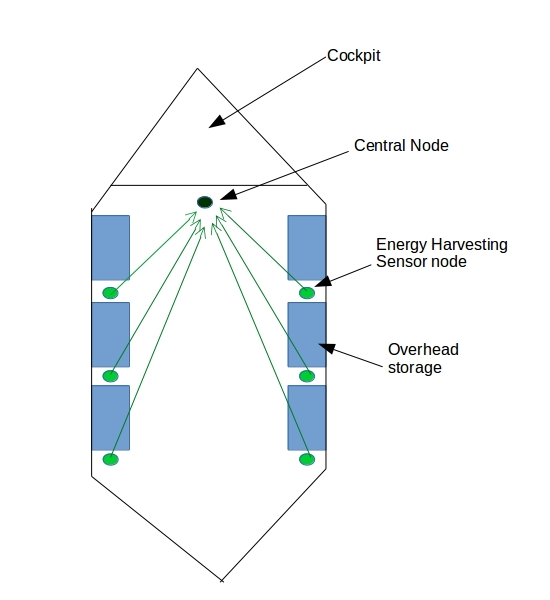
Bluetooth Low Energy (BLE) Protocol EH WSNs
The aim of the project is to design and deploy an energy harvesting wireless sensor network for airplane environments. Specifically, we are interested to increase the security features in an airplane by monitoring the status of the overhead storage using energy harvested sensor nodes. In order to save energy further, the sensor nodes use Bluetooth-Low-Energy (BLE) protocol for communication. As a result of lack of professional BLE simulators, our task is to develop the BLE protocol module in Network Simulator-3 (NS-3). Our next objective is to study the feasibility of such an energy efficient network for a given scenario.
Members: Debanjan Sadhukhan, Chinmay Bhat
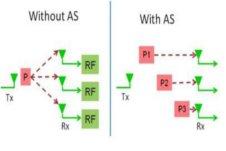
Antenna selection (AS) provides a low hardware complexity solution for exploiting the spatial diversity benefits of multiple antenna technology. In receive AS, the receiver does not receive and process signals from all its receive antennas. Instead, it dynamically selects a subset comprising antennas with the best instantaneous channel conditions to the transmitter, and only processes signals through them. This enables the receiver to employ fewer expensive radio frequency (RF) chains, which consist of components such as a low noise amplifier (LNA), down-converter, and analog-to-digital converter (ADC). Similarly, in transmit AS, the transmitter employs fewer transmit RF chains than the available number of antennas. In addition to its lower complexity, AS is attractive because it provably achieves full diversity order, i.e., it provides as much robustness against fading in wireless channels as a full complexity receiver.
Our research has focused on training for receive antenna selection. The training procedure is the crucial first step that enables AS in practice. It is through training that the receiver estimates the channel gains of the various antennas and determines which antenna subset to select. The inevitable presence of noise during the estimation process and the time-varying nature of the wireless channel can lead to inaccurate selection and incorrect data decoding, both of which together increase the overall symbol error rates (SERs) observed in the system.
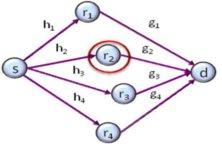
Cooperative communications is a promising technology in which different wireless nodes help each other at the physical and multiple access layers in forwarding messages to their intended recipients. Doing so enables the wireless networks to exploit their inherent geographically distributed nature and their large coverage.
In a relay-based multihop cooperative wireless network, such as the one shown in Fig. 2, one or more relays forward a message from the source to the destination. Ideally, having more relays to forward a message helps improve performance. However, this is practically difficult since tight symbol-level synchronization needs to be ensured at all the separated relays. Selection is a solution that solves this problem. In selection, depending on the current channel realizations, only the best relay, which is the one that has the most favourable channel realization, is selected to forward the message. Selection circumvents the synchronization problem since only the selected node transmits. Yet, despite its simplicity, it achieves the highest diversity order - as was also the case with antenna selection
Splitting-based selection: The splitting-based selection algorithm, which we analysed, is a time-slotted multiple access contention algorithm in which each node autonomously decides whether or not to transmit in a certain time slot. This decision by a node is based on its local channel gain knowledge, which is captured in the form of a real-valued metric. In each slot, only those nodes whose metrics lie between two thresholds transmit. At the end of every slot, the controller feeds back a three-state outcome indicating idle (when no node transmitted), success (when exactly one node transmitted and was decoded successfully), or collision (when two or more nodes transmitted and none could be decoded). The nodes update their thresholds in each slot based on the feedback from the coordinator. The algorithm guarantees that the first node to successfully transmit to the controller is the best node, i.e., the one with the highest metric among all the nodes.
The splitting-based selection algorithm is attractive because it is extremely fast. For example, it can select the best node in just 2.47 slots on average, even in the worst case where the number of available nodes is infinity. It can be speeded up even further by using power control.
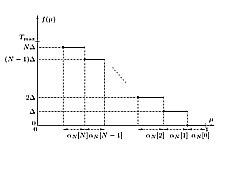
Timer-based selection: The timer-based selection algorithm instead uses a back-off timer mechanism to select the best node. Every node sets its timer as a function of its metric and transmits a packet when its timer expires. The key idea is that the metric-to-timer mapping is a deterministic monotone non-increasing function. This is enough to ensure that the first node that transmits is the best node. The timer-based selection algorithm is attractive because of its simplicity and its distributed nature. However, if two timers that expire within a time Δ of each other collide and cannot be decoded. Therefore, the performance of the algorithm is fundamentally constrained by the vulnerability window, Δ.
Unlike the splitting-based algorithm, it requires no feedback during the selection process. The optimal metric-to-timer mapping, which maximizes the probability of selection success given a pre-specified maximum duration of selection Tmax, was derived by us. It was shown to be a practically feasible staircase mapping, which is depicted in Fig. 3. The optimal 'stair' lengths, as shown in the figure, were also derived.
Selection and Data Transmission Trade-off: In every cooperative system that uses selection, one invariably faces a fundamental trade-off that is related to the selection duration. The larger the selection duration, the more accurate the selection. However, this reduces the relative fraction of time available for data transmission using the selected node. On the other hand, shrinking the selection duration increases the odds that the selection algorithm fails to select the best node. As a result, the system loses out on the spatial diversity benefits of selection. This trade-off was addressed by us. We considered both non-adaptive and adaptive rate and power modes of transmission, and showed that the selection process is often far from ideal and perfect at the optimal system operating point. This is unlike what has been assumed in the literature.
Energy harvesting (EH) networks offer the possibility of a maintenance-free and perpetual network operation. In these networks, the nodes harvest energy from the environment using solar, vibration, thermoelectric effects, and other physical phenomena. Unlike conventional battery-powered nodes that die once their pre-charged batteries drain out, an energy harvesting node can harvest energy and remain available - essentially forever. This is possible provided the communication protocols can be engineered to ensure that no more energy is drained than has been harvested. The use of the energy harvesting functionality motivates a significant redesign of the physical and multiple access communication protocols. This is because minimizing energy consumption ceases to be the dominant goal in the design of the protocols. Instead, the problem requires handling the randomness in the energy harvested and ensuring that the energy required for communication and sensing needs, if any, can be met. Further, the inclusion of even a few energy harvesting nodes promises significant improvements in the lifetime of conventional wireless networks.
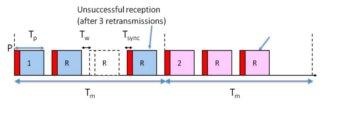
A simple theoretical model that captured the interactions between important parameters that govern the communication link performance of a single EH node was developed. In this work, each EH node is allowed a fixed number of retransmission attempts to send information to a destination, as shown in Fig. 4. Unlike conventional nodes, the packet may not reach the destination (outage) not only because of fading and noise in the communication channel but also because transmission did not take occur due to insufficient energy stored in the battery. The outage probability analysis developed brings out the critical importance of the energy profile and the energy storage capability on the EH link performance. The insights turn out to be different for slow and fast fading channels. The analysis showed that properly tuning the transmission parameters of the EH node and having even a small energy storage capability considerably improves the EH link performance.
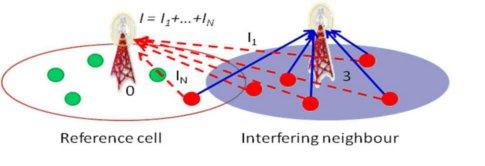
Interference plays a crucial role in code division multiple access (CDMA) based cellular communication systems, which use pseudo-random spreading codes for transmitting data. Therefore, an accurate characterization of the statistics of interference is an essential first step in cellular system design and analysis. While downlink co-channel interference is well characterised, the same is not true for uplink interference from neighbouring cells. This is because the interfering signals from the neighouring cells undergo shadowing and fading in their respective wireless channels. The number of interfering signals is random since the number of users per cell that generate them is random. Power control and cell selection, which affect the interfering users� transmit powers, further exacerbate this randomness. An alternate characterization of the uplink co-channel interference was developed by us. It showed that the lognormal distribution characterizes the uplink interference statistics well, and is significantly better than the conventionally assumed Gaussian distribution.